с 01.01.1993 по 01.01.2019
Сибирский федеральный университет (Базовая кафедра цифровых финансовых технологий Сбербанка, доцент)
с 01.01.2007 по настоящее время
Красноярск, Красноярский край, Россия
Красноярск, Красноярский край, Россия
с 01.01.2019 по настоящее время
Красноярск, Россия
ГРНТИ 06.52 Экономическое развитие и рост. Прогнозир-ние и планирование экономики. Экономич. циклы и кризисы
ГРНТИ 06.73 Финансовая наука. Денежные и налоговые теории. Кредитно-финансовые институты
ОКСО 38.02.07 Банковское дело
ОКСО 38.04.02 Менеджмент
ББК 6523 Планирование. Экономическое прогнозирование
ББК 6526 Финансы. Денежное обращение
BISAC BUS000000 General
На основе анализа текущего состояния кибер-рисков в финансовой среде (как в России, так и за рубежом) была отмечена разрозненность подходов к оценке, моделированию и прогнозированию кибер-рисков. Исследование показало возможность использования эконометрических моделей для прогнозирования кибер-атак, при этом необходимо понимать, что во временной перспективе данные модели должны работать эффективнее, так как предполагается наращение статистических данных, что сделает прогнозы более точными и вероятностными. Перспективы дальнейшей имплементации и совершенствования очевидны в связи с актуальностью вопроса и его степенной разработки.
Кибер-атака, кибер-риск, финансовые институты, DDoS-атаки, моделирование кибер-атак
The researches show that the cyber-risk has arisen as a systemic risk concern, following recent cyber incidents. Recent surveys point to cyber-risk as a main concern among market participants ranked first in the DTCC Systemic Risk Barometer (Figure 1), and second in the 2017 H2 systemic risk survey by the Bank of England (Bank of England (2017)). Successful cyber-attacks such as Wannacry in May 2017 or NoPetya in June 2017 have shown that cyber-attack can lead to severe disruptions and major losses for the targeted firms.
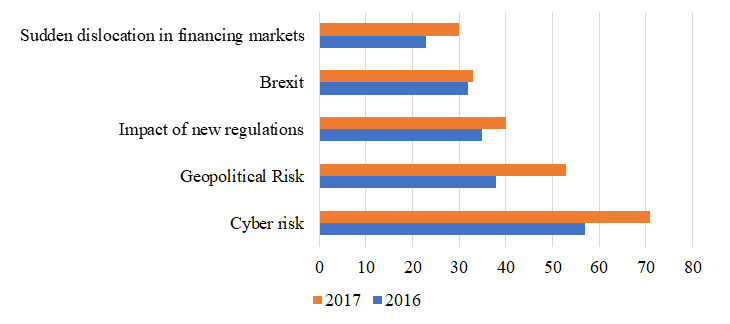
Figure 1 – Risk to broader economy
Data on cyber incidents is scarce and there have been very few quantitative analyses of cyber-risk. Data on cyber-risk is notoriously scarce, since there is no common standard to record them, and firms have no incentives to report them. For example, in the U.K. only 49 cyber-attacks were reported in 2017 to U.K. Financial Authorities, pointing to a material under reporting of successful cyber-attacks in the financial sector. Moreover, international sharing of data reported to domestic regulators also must take into account that there might be national security considerations in sharing and reporting of data.
In the U.S., the SEC released in 2011 guidance on disclosure of cyber-risk for listed firms (SEC (2011)), which was revised in 2018 to provide additional details on how and when firms should disclose the information to investors (SEC (2018)). However, there is scope to provide a framework to report cyber-attacks, which could better address existing data gaps.
For example, among around 4,000 annual reports for U.S firms (‘form 10-K’) published in 2017, only 7 % included a reference to cyber-risk, mainly in the finance and services sectors (Figure 2).

Figure 2 – Cyber risk awareness by sectors in the U.S.
In the European Union, the General Data Protection Regulation (GDPR), which will enter into force in May 2018, requires firms to report breaches to the competent supervisory authority within 72 hours. Failure to comply with the reporting requirements could lead to fines up to 20 million of euro or 4 % of global annual turnover.
The financial sector is one of the most targeted sectors due to its reliance on information and its central role in the credit intermediation process. Moreover, due to regulatory requirements regarding operational risk, financial institutions are more likely to collect data on cyber incidents than non-financial corporates.
It is important to consider the problem of cyber-risk for financial institutions using publicly available data and commercial data sets, with potential use by regulators, supervisors and financial institutions.
Cyber-risk can be defined as “operational risks to information and technology assets that have consequences affecting the confidentiality, availability, or integrity of information or information systems”. Compared to risk categories covered by insurance, cyber-risk shares characteristics with both property and liability risk, as well as catastrophic and operational risk.
On the one hand, cyber-risk can impact first (the target) and third parties (a counterpart to the target). On the other hand, losses due to cyber-risk are frequently small and independent but they could also have a low frequency and a high impact (‘blackout scenario’). Cyber-risk can be unrelated to cyber-attacks: for example, software updates or natural disasters can lead to the crystallization of cyber-risk through business disruptions without any nefarious intent, as outlined in the definition of cyber incidents.
Cyber-attacks can impact firms through the three main aspects of information security: confidentiality, integrity and availability. Confidentiality issues arise when private information within a firm is disclosed to third parties as in the case of data breaches. Integrity issues relate to misuse of the systems, as is the case for fraud. Finally, availability issues are linked to business disruptions. The three types of cyber-attacks have different direct impacts on the targets: Business disruptions prevent firms from operating, resulting in loss revenue; fraud leads to direct financial losses; while the effects of data breaches take more time to materialize, through reputational effects as well as litigation costs. More generally, the risk of a loss of confidence following cyber-attacks could be high for the financial sector, given the reliance of financial institutions on the trust of their customers. Regarding the financial system, business disruptions are more likely to have direct short-term contagion effects than fraud or data breach, which tend to impact mainly the targeted firm in the short-term.
The financial sector is highly exposed to cyber-risk, across all types of countries. The International Telecommunication Unit (ITU), which is an agency of the United Nations, provides a global cybersecurity index for the world. Their index is based on a range of factors, including legal, technical and organizational arrangements as well as capacity building and cooperation (ITU, 2017). The cross-country heterogeneity regarding cybersecurity, with most Advanced Economies and Emerging Markets having a high value of the cybersecurity index (above the median), while middle income and low-income countries tend to have lower values.
Since today there is no quantitative measure of cyber-risk by country for the financial sector, it is only possible to build an indirect measure using media coverage. An index is computed using the number of articles referring to cyber-risk by country, divided by the number of articles referring to risk in the financial sector. As shown in the map, almost all countries are covered. The index is highest in countries that recently suffered from cyber-attacks such as Bangladesh and the Baltic states.
Complete data on cyber-attacks is notoriously scarce. Available public and commercial datasets exist but they are incomplete, have different coverage and use different definitions of cyber-attacks, which makes the analysis of cyber losses difficult. Moreover, data on losses are gathered from different sources and using different methods (actual costs, estimated costs etc.) making their comparability difficult. Among non-public datasets, two main types are available: commercial data and consortium data. Commercial data providers such as SAS or IBM collect data on operational risk events, which includes cyber events based on publicly available information.
Consortium data is provided by ORX, a consortium of financial institutions that gathers data on operational risk events. ORX members provide anonymized data covering around 600,000 risk events which is available to members only. ORX also provides a dataset based on publicly available data, ORX News, which covers around 6,000 events, including cyber events related to cyber-attacks. Data on losses includes only direct losses, although indirect losses (reputation, business recovery and remediation etc.) account for more than 90 % of total losses.
Based on the limited dataset, advanced economies are the main targets of cyber-attacks but EM and developing economies are also exposed to cyber-risk (Figure 3), based on data from ORX News. AEs account for 80 % of successful attacks, mainly in the U.S. (39 %) and UK (7 %) as shown in Figure 6. Among EMs, the BRICS account for most of the attacks (17 %), mainly in Russia (6 %), China (4 %) and India (3 %). Overall, financial institutions in more than 50 countries have been victims of cyber- attacks over the last few years according to reports in the public media.

Figure 3 – Share of cyber-attacks on Financial Institutions by country (% of total)
Among financial institutions, banks account for the bulk of the attacks (91 % of the attacks), followed by insurance companies (7 %). Among banks, retail banking activities (39 % of the total) and credit cards services (25 %) were the main business lines targeted.
Central banks in AEs and EMs have also been the victims of cyber-attacks. In AEs, attacks were either data breaches (U.S., Italy) or business disruptions (Norway, Sweden), while in EMs, most attacks were related to fraud, resulting in losses of USD 117 million (Table 1).
Table 1 – Recent cyber-attacks on central banks
|
Institution |
Year |
Type of attack |
Details |
|
Federal Reserve Bank of Cleveland |
2010 |
Data breach |
Theft of 122,000 credit cards |
|
Federal Reserve Bank of New York |
2012 |
Data breach |
Theft of proprietary software code worth USD 9.5 Million |
|
Sveriges Riksbank |
2012 |
Business Disruption |
Distributed Denial of Service (DDoS) attack left the website offline for 5 hours |
|
Banco Central del Ecuador |
2013 |
Fraud |
USD 13.3 Million stolen from the account of the city of Riobamba at the central bank |
|
Federal Reserve Bank of Saint Louis |
2013 |
Data breach |
Publication of credentials of 4,000 US bank executives by Anonymous |
|
Central Bank of Swaziland |
2014 |
Fraud |
Theft of USD 688,000 |
|
ECB |
2014 |
Data breach |
20,000 email addresses and contact information compromised |
|
Norges Bank |
2014 |
Business Disruption |
DDoS attack on seven large financial institutions, resulting in suspended services during a day. |
|
Central Bank of Azerbaijan |
2015 |
Data breach |
Theft of thousands of bank customers’ information |
|
Bangladesh Bank |
2016 |
Fraud |
The SWIFT credentials of the Bangladesh central bank were used to transfer USD 81 Million from its account at the FRBNY. Hackers tried to steal USD 951 Million. |
|
Bank of Russia |
2016 |
Fraud |
21 Cyber-attacks aimed at stealing USD 50 Million from correspondent bank accounts at the central bank, resulted in a loss of USD 22 Million. |
|
Bank of Italy |
2017 |
Data Breach |
Hack of email accounts of two former executives. |
Among cyber-attacks, fraud and data breaches are more prevalent, yet business disruption is also significant. In the ORX News dataset, fraud accounts for 43 % of events, data breaches 34 % and disruption 23 %. While business disruptions are known immediately, the other types of cyber-attacks can take place for months or years before being noticed and reported, which could lead to a downward bias in the dataset.
Patterns can be identified for each type of cyber-attacks using text-mining techniques applied to the ORX News dataset, which provides for each case background information in text form. More precisely, correspondence analysis, a statistical technique to provide a graphical representation of the structure of a dataset, is used to identify the words which tend to cluster around the three types of cyber-attacks. Business disruption is associated with DDoS attacks which typically impact the website of the target, when a very large number of requests are sent to the targeted servers, overloading the system and making it unable to operate.
Data breaches are linked with credit card information, and fraud is associated with money transfers, and a loss amount – since around 80 % of the events with loss data are cyber-related fraud. The word “bank” is in the middle of the chart since banks are the main targets of all three types of attacks. The x-axis can be interpreted as a measure of the informational content regarding losses (with most events in the business disruption category having no loss information), while the y-axis measures whether the impact of the cyber-attack is immediate (business disruption or fraud) or takes more time to materialize, as in the case of data breaches (Figure 4).
So here a question arises: why are financial institutions highly exposed to cyber-risk? In information security risk management, risk is defined as a combination of consequences and likelihood, where likelihood is a function of threat levels and the ease of exploitation of existing vulnerabilities
Risk = f (Threat, Vulnerability, Consequences),
In this context, financial institutions are highly exposed to cyber-risk due to a combination of factors. Threat levels are particularly high for financial institutions due to cybercrime, hacktivism, proxy organizations–sophisticated attackers conducting espionage on behalf of a beneficiary, and surveillance of communication by third parties. Vulnerabilities to cyber incidents (including cyber-attacks) can be considered high because financial institutions are dependent on highly interconnected networks and critical infrastructures. Moreover, many institutions have legacy systems which might not be resilient to cyber-attacks. The increased level of sophistication of cyber criminals, along with the decline in the cost of launching cyber-attacks, make institutions with legacy systems all the more vulnerable. Consequences of cyber-attacks are also high because financial activity is dematerialized and therefore highly dependent on technology.
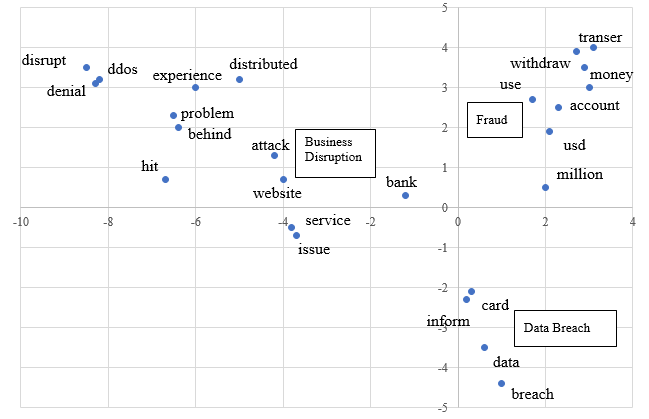
Figure 4 – Correspondence analysis (terms contributing the most by types of attack)
Financial institutions are particularly exposed to cyber-risk due to their reliance on critical infrastructures and their dependence on highly interconnected networks. Critical financial market infrastructures include payment and settlement systems, trading platforms, central securities depositories, and central counterparties. The critical infrastructures represent a Single Point of Failure and any successful attack could have wide-ranging consequences.
A business disruption of a financial market infrastructure or a set of large financial institutions could have a significant impact due to risk concentration and the lack of substitutes in the case of Financial Market Infrastructures (FMIs). If a payment and settlement systems go offline during the day, market participants would be unable to process transactions and therefore be exposed to liquidity and solvency risk. Similarly, if one or several large banks are disrupted and unable to process transactions, their counterparts would be subject to liquidity and solvency risk.
Several papers have already looked at the impact of a disruption of a large market participant on FMIs. For example, Clarke and Hancock (2014) use the Bank of Finland payment simulator to analyse the impact of operational disruptions of the largest fifteen participants on intraday liquidity in the Australian Real Time Gross Settlement system. Their results show that the amount of unsettled payment varies according to the time of disruption and the participants size. Similarly, as part of their risk management framework, Central Counterparties (CCPs) – and their supervisors–regularly assess the impact of events that could be the result of a cyber-attack leading to the business disruption of clearing members. For example, the recent stress tests of CCPs run by the European Securities and Markets Authority (ESMA) estimates the impact of the default of two large clearing members on the CCP (credit risk) and the consequences of the failure of a custodian (liquidity risk). To some extent, the stress test framework can also be used to model the impact of a successful cyber- attack on market participants.
The disruption of material infrastructures such as power grids and IT infrastructures (Cloud providers or operating systems) could also have a large macroeconomic impact. Recent studies estimate that a disruption of part of the U.S power grid could lead to up to USD 1 trillion in losses and a disruption of IT infrastructures up to USD 53 billion (Table 2).
Table 2 – Impact of disruption of infrastructures (all sectors)
|
Scenario |
Target |
Losses (in billion of USD) |
|
Electricity blackout |
Energy infrastructures |
243-1 024 |
|
Cloud Service Providers hack |
Cloud Providers |
5-53 |
|
Mass vulnerability attack |
Operating System |
10-29 |
Successful attacks on a financial institution could result in significant disruptions, although to date attacks have not caused large damages, based on publicly available information. A common method to disrupt firm business operations is to launch a DDoS attack on the targeted firms’ servers. For example, on August 10 and 11, 2011, the news website of the Hong Kong stock exchange suffered a Distributed Denial of Service (DDoS) attack. The stock exchange had to suspend trading in the shares of seven companies due to make interim results announcements as the result of the attack. No significant damages have been reported so far, as business disruptions were short-lived (from a few hours to a day or two) and only affected part of banks’ business operations (website and sometimes online payments). A recent report by Lloyd’s estimates that a disruption of the top cloud provider in the U.S. for 3 to 6 days could lead to losses of around USD 24 billion, with most losses occurring in the manufacturing and trade sectors, while losses for the financial sector would be limited to USD 450 Mn.
Cyber-attacks can also be used to undermine customers’ confidence in an institution. For example, on June 27, 2014, Bulgaria’s largest domestic bank FIB experienced a depositor run, amid heightened uncertainty due to the resolution of another bank, following phishing emails indicating that FIB was experiencing a liquidity shortage. Deposits outflows on that day amounted to 10 % of the banks’ total deposits and the bank had to use a liquidity assistance scheme provided by the authorities.
Cyber-attacks can also target multiple financial institutions to disrupt the financial sector. Several countries have been exposed to coordinated cyber-attacks on the banking sector using DDoS, although no significant damages have been reported, they are reflected below (Table 3).
Table 3 – DDoS attacks on multiple financial institutions
|
Country |
Attack |
|
US |
In September 2012, the websites of Bank of America, PNC, JPMorgan, US Bancorp, Wells Fargo were targeted and one month later the websites of BBT, Capital One, HSBC, Region Financial, SunTrust were also disrupted. |
|
Czech Republic |
On March 6, 2013, the websites of the central bank, three large banks and the stock exchange were disrupted, with limited damages estimated at USD 0.5 Million |
|
Norway |
On July 8, 2014, seven major financial institutions were attacked, leading to disrupted services during the day. |
|
Finland |
End-2014, three banks (Op Pohjola, Danske Bank and Nordea) suffered DDoS attacks that rendered their online services unavailable and for one bank prevented customers from withdrawing cash and making card payments. |
Cyber-attacks can be used for fraudulent purposes, as evidenced recently by theft using SWIFT. Access to confidential information, including clients’ credentials used for online payment can be used by cyber-criminals. In the dataset, cyber-related fraud accounts for 90 % of reported losses.
Over the last three years, at least ten attacks were based on the SWIFT system– a messaging system used by financial institutions for financial transactions (Table 4). Hackers accessed the victims’ SWIFT credentials and sent fraudulent payment orders on behalf of the target (EM banks) to the hackers’ bank accounts–in some cases transiting through AE banks and central banks. Initial losses amounted to USD 336 Million, while actual losses were around USD 87 Million, as some orders were frozen and some money was recouped.
Emerging technologies such as Fintech are also particularly exposed to cyber-attacks given their reliance on technology. Technological innovations may increase vulnerabilities to cyber-attacks, as specialized firms might have fewer controls and risk management procedures than large, vertically integrated regulated intermediaries (IMF). Greater use of technology could also expand the range and numbers of entry points into the financial system, which hackers could target. Fintech activities could also increase third-party reliance, where firms outsource activities to a few concentrated providers. In this case, the disruption of a provider could increase systemic risk due to the centrality of the provider in the financial system. Cyber-attacks on Fintech firms (mainly online exchanges allowing the trading of Bitcoins and providing wallet services) have resulted in at least USD 1,450 million in losses due to fraud since 2013 (Table 4).
Table 4 – Cyber-attacks using SWIFT
|
Institutions |
Date |
Initial losses (USD million) |
Current estimated losses* (USD million) |
|
Banco del Austro (Ecuador) |
Jan. 2015 |
12.2 |
9.4 |
|
Bangladesh Central Bank |
Feb. 2016 |
81 |
66 |
|
Union Bank of India |
Jul. 2016 |
171 |
0 |
|
TP Bank (Vietnam) |
May 2016 |
1 |
0 |
|
Akbank (Turkey) |
Dec. 2016 |
4 |
4 |
|
Far Eastern International Bank (Taiwan, Province of China) |
Oct. 2017 |
60 |
0.5 |
|
NIC Asia Bank (Nepal) |
Oct. 2017 |
4.4 |
0.6 |
|
Globex (Russia) |
Dec. 2017 |
1 |
0.1 |
|
Unidentified bank (Russia) |
Dec. 2017 |
Unknown |
6 |
|
City Union Bank (India) |
Jan. 2018 |
2 |
Unknown |
The high degree of interconnectedness across firms can lead to rapid contagion effects. For corporates, due to the high interconnectedness across supply chains, a successful attack on part of the network could spread rapidly to other firms. For example, in June 2017, a ransomware targeting Ukraine lead to losses of at least USD 1.3 billion for multinational firms across sectors (transportation, construction or food) linked to Ukrainian companies. For financial institutions, a disruption of one large bank, making it unable to process transactions and post margins could spread quickly to its counterparties and the financial market infrastructures, resulting in heightened liquidity and solvency risk.
Table 5 – Cyber-attacks on Fintech firms
|
Institution |
Date |
Estimated losses (USD Mn) |
|
Inputs.io |
Oct. 2013 |
1.3 |
|
GBL |
Oct. 2013 |
5 |
|
Bitcoin Internet Payment Services |
Nov. 2013 |
1 |
|
MT Gox |
Jan. 2014 |
470 |
|
BitPay |
Dec. 2014 |
1.9 |
|
EgoPay |
Dec. 2014 |
1.1 |
|
Bitstamp |
Jan. 2015 |
5.3 |
|
Bitfinex |
May. 2015 |
0.3 |
|
Gatecoin |
May 2016 |
2 |
|
DAO Smart Contract |
Jun. 2016 |
50 |
|
Bitfinex |
Aug. 2016 |
72.2 |
|
CoinDash |
Jul. 2017 |
7 |
|
Tether |
Nov. 2017 |
31 |
|
NiceHash |
Dec. 2017 |
64 |
|
Coincheck |
Jan. 2018 |
534 |
|
BitGrail |
Feb. 2018 |
170 |
|
Coinsecure |
Apr. 2018 |
33 |
Financial institutions are also particularly vulnerable to data breaches. Given their reliance on customer’s data to conduct business, the financial sector suffered the most incidents with data loss in recent years– including the Equifax data breach where hackers may have stolen personal information of more than 145 million U.S customers. The economic impact of data breaches is hard to assess since indirect effects (loss of clients, reputation risk) are likely to be more material than direct effects (recovery and litigation costs). In the U.S. alone, more than 260 million records were breached due to hacking over the last three years in the financial sector (Figure 5). The Ponemon Institute estimates that the average cost per stolen record was USD 141 in 2017. Applying the Ponemon estimates, losses due to data breach over the last three years would be around $38 billion for U.S. financial firms alone.

Figure 5 – Number of records breached in the financial sector in the U.S. (in million)
It is necessary after market research to analyse the cyber-risks management practice in banking system that we have today to investigate current methods of assessment and forecast.
To prove the necessity the econometric models of cyber-risk forecast in Russia was build.
One of the biggest banks of Russia, Sberbank, conforms to the international standards and everyday activity of the bank is closely connected with usage of the modern computer technologies. What is more Sberbank is in very crucial dependence on reliable and trouble-free operation of electronic computing systems. As the world practice shows, there are many facts which testify to rather strong vulnerability practically of any company as cybercrimes are not limited with the territory barriers. Therefore, hackers have a potential opportunity to equally threaten information systems in any country.The main tools of cyber-fraudsters are:
- Virus programs
- DDoS-attacks
- Fraudulent schemes of theft of money from debit and credit cards.
- Counteraction to the DDoS-attacks
It is possible to look at Sberbank as at an example, because in 2018 it reflected about 90 DDoS, 25 of those attacks had very high power, that was reflected by Sberbank in the report on it "Bank trends – 2018".
It follows from this report that the level of the DDoS-attacks on electronic devices of Sberbank grew by one and a half times in comparison with 2017. Nearly every week on the e-mail addresses of bank about 14.5 thousand letters come with virus programs. During 2018 Sberbank was exposed on average two of the DDoS-attacks in a week. These attacks had an external impact on electronics of bank which cause strong overloads. As a result of such attacks, the full stop of work of all systems of Sberbank is quite probable.
In the course of the research we carried out calculation in which by means of the analysis of already available data we revealed an approximate trend of the DDoS-attacks, one of main types of cyber-attacks, on the basis of reporting data on the number of the DDoS-attacks from 3rd quarter 2015 to the 3rd quarter 2017.
Process of creation of model represents set of the following stages:
- Creation of the required equation of dependence of a look: y=a+bt.
- Calculation of expected values
and to define an error of the carried-out regression of e.
- Calculation for the corresponding formulas determination coefficient.
- Check of the importance of the received regression coefficients on the basis of Styyudent's t-criterion.
- Check of the importance of the received equation based on F-criterion.
- Testing of autocorrelation of the remains.
As a result, the expected data on the DDoS-attacks provided in table 6 were obtained. Proceeding from which, it is possible to claim that the expected trend of emergence of the DDoS-attacks does not demonstrate their decrease.
During the time from 3rd quarter 2015 to the 3rd quarter 2017 (information available on the official site of the Bank of Russia) and also the forecast calculated by means of application of model we can observe the following dynamics illustrated in (Figure 6).
Table 6 – Calculation of expected data on the DDoS-attacks
|
Date No. of quarter (ti) |
No. of quarter (ti) |
Quantity attacks (yi) |
Forecast (ŷ) |
Mistake (ei) |
|
|
|
|
3 кв. 2015 |
1 |
3 |
6 |
-3 |
10 |
10 |
16 |
|
4 кв. 2015 |
2 |
12 |
6 |
6 |
75 |
31 |
9 |
|
1 кв. 2016 |
3 |
4 |
7 |
-3 |
70 |
8 |
4 |
|
2 кв. 2016 |
4 |
2 |
7 |
-5 |
6 |
27 |
1 |
|
3 кв. 2016 |
5 |
5 |
8 |
-3 |
7 |
7 |
0 |
|
4 кв. 2016 |
6 |
20 |
8 |
12 |
214 |
146 |
1 |
|
1 кв. 2017 |
7 |
8 |
8 |
0 |
153 |
0 |
4 |
|
2 кв. 2017 |
8 |
12 |
9 |
3 |
13 |
11 |
9 |
|
3 кв. 2017 |
9 |
2 |
9 |
-7 |
107 |
49 |
16 |
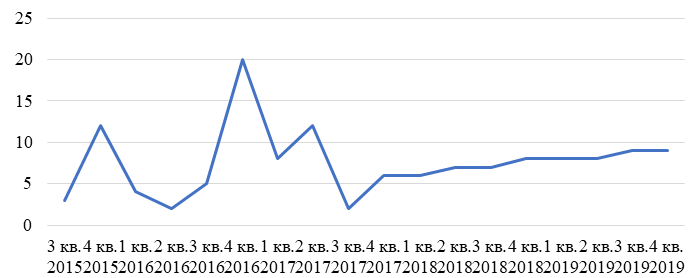
Figure 6 – Dynamics of the DDoS-attacks
Thus, by means of application of this method of calculation it is possible to predict potential dynamics of cyber-attacks that in the future will become necessary to put the necessary sums which size will estimate incidents, in an indicator of capital adequacy and, in case of collision with cyber-risks, to be ready to financial losses.
1. Assessment and Minimization of Risks to the Budgets of Russia’s Regions / Makarova S.N., Cherkasova Y.I., Gordeeva G.P. // Asian Social Science; № Vol. 11, No. 8; 2015. P. 284-291
2. Camillo M., Cybersecurity: Risks and management of risks for global banks and financial institutions // London, UK, 2016;
3. Cebula, J. J. and Young, L. R. (2010): A Taxonomy of Operational Cyber Security Risks, Technical Note CMU/SEI-2010-TN-028, Software Engineering Institute, Carnegie Mellon University.
4. Cyber-risk and regulation in Europe: A new paradigm for banks. Centre for regulatory strategy EMEA.2018, p. 16.
5. Deloitte, 2016, “Beneath the Surface of a Cyberattack”, Deloitte U.S.A., Cyber Risk Services.
6. Friedman, S., 2016, “Taking cyber-risk management to the next level- Lessons learned from the front lines at financial institutions”, Deloitte Insight, June.
7. Gracie A., 2014, “Managing cyber-risk - the global banking perspective”, Bank of England.
8. J. Wahlström, Operational Risk Modelling: Theory and Practice // Royal Institute of Technology, Stockholm, Sweden. 2013;
9. Romanosky, S., 2016, “Examining the costs and causes of cyber incidents”, Journal of Cybersecurity, Vol. 2 (2).
10. Yankina I. And the Analysis of susceptibility to operational risk of commercial banks in Russia / I.A. Yankina, E.E. Dolgova//Finance and the credit. 2016. No. 3 (675). p. 17-28.














